BİLGEM
Public Key Infrastructure
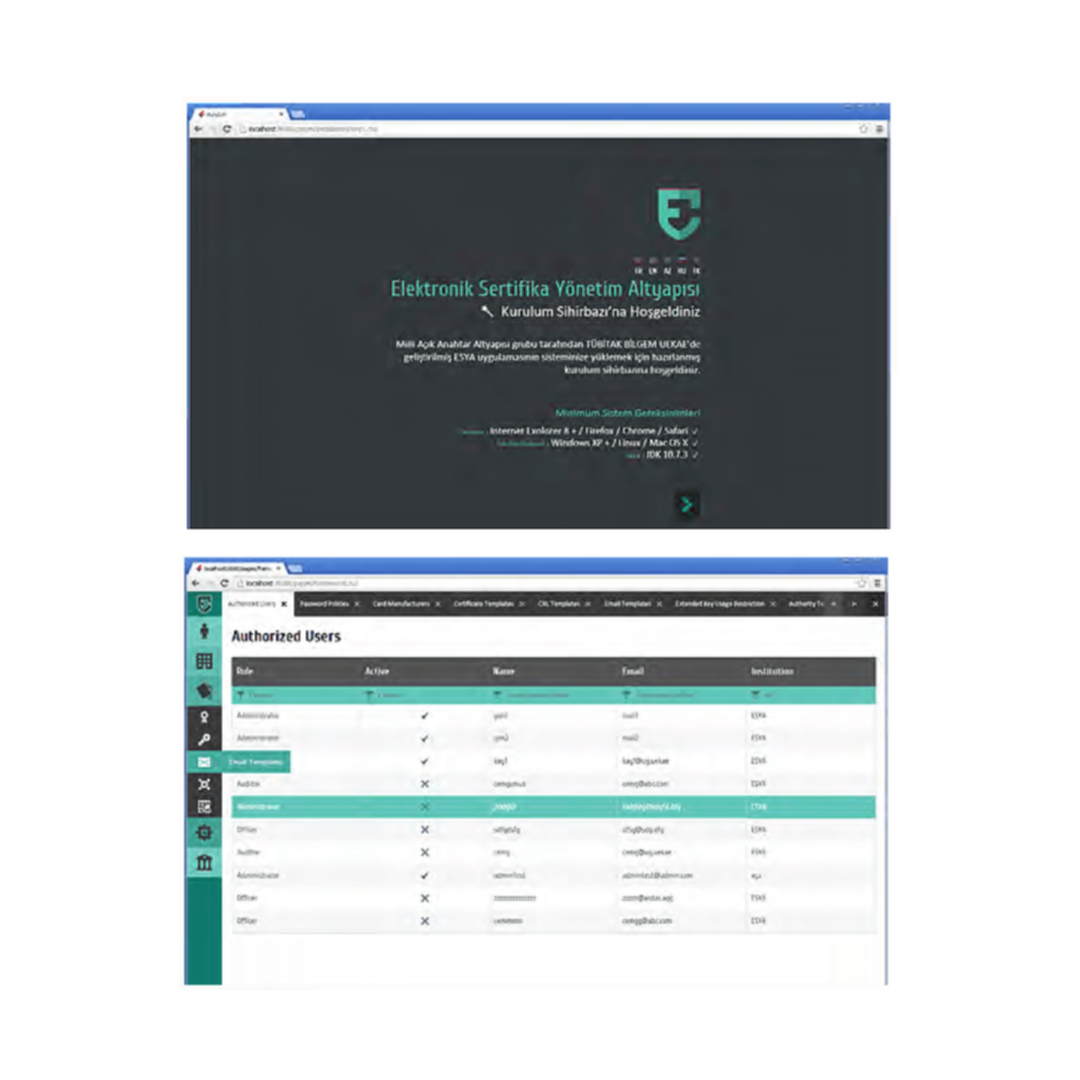
ESYA SM - Electronic Certificate Asst. Infrastructure Certification Authority
- Product information
- Public Key Infrastructure Services
- Technicial Features
- 509 v3 certificates, X.509 v2 certificate revocation lists (CRL/CRL)
- Online Certificate Status Protocol (CISDUP/OCSP)
- Key recovery and renewal
- Ability to manage certificate lifecycle processes for User, Device, Institution and Role records (certification, certificate suspension, certificate revocation, password change and information update)
- Production of Qualified Electronic Certificates (in accordance with Electronic Signature Law No. 5070)
- SSL generation with Certificate Transparency support
- SSL (Server and client), VPN certificate generation,
- Easy integration with external systems with RESTful web service infrastructure,
Windows Smartcard Logon, Windows Domain Controller certificate generation
Crypto Features
- RSA algorithm (1024, 2048, 4096 bit key length)
- ECDSA algorithm (163, 192, 256, 368, 431, 512, 521 bit key lengths)
- SHA-1, SHA-256, SHA-384, SHA-512 message digest algorithms
Crypto Hardware Support
- Working with PKCS11 compatible smart cards and sticks
- Using HSM (Hardware Security Module)

KERMEN - Public Key Infrastructure Desktop Client
- Product information
- Technicial Features
As a result of the widespread use of the Internet and computer systems, institutions and organizations have moved most of their work and services to the computer environment and have started to use the Internet as an effective communication channel. In this context, the use of e-mail and the amount and importance of the information it carries are increasing day by day. Leaving valuable information stored in files on work computers or transported on the Internet through channels such as e-mail unprotected against unauthorized access can cause commercial losses and weaken the reliability and brand value of organizations. Because of these, institutions need desktop security solutions for workstations, desktop and portable computers and secure communication ways over the internet.
Key Components
- Secure email module
- Desktop security module
- Kermen
Sur Security Solutions
- Secure email (SMIME)
- File signing/encryption
- Secure directory
- Certificate validation
- Secure Erase
Crypto Features
- Working with X.509 v3 certificates prepared with RSA, DSA and elliptic curve algorithms
- Use of 3DES, AES algorithms for PKCS7/CMS
- SHA-1 and SHA-2 family message digest algorithms
- PKCS12 and PKCS5 password-based encryption algorithms
Crypto Hardware Support
- Working with PKCS11 compatible smart cards and sticks
- Retrieve keys with PFX files and securely store/use in local storage when no smart card/stick is used
ESYA API / Electronic Signature Libraries
- Product information
- Features
- Technicial Features
MA3 API E-Signature Software Libraries have been produced with BİLGEM's e-signature experience of more than 20 years and allow signing transactions to be done quickly and securely with their easy-to-use interfaces whose security and standards have been determined. Software libraries have been developed for Java and .NET platforms in order to easily integrate e-signatures into software.
Supported Standards
- Electronic signature format (ASN data structure) in ETSI TS 101 733 CADES standard
- Electronic signature format (XML data structure) in ETSI TS 101 903 XADES standard
- Electronic signature format in ETSI TS 102 918 ASIC standard
- Electronic signature format (PDF data structure) in ETSI 102 778 PADES standard
Supported Signature Types
- Basic signature (ES-BES)
- Timestamped signature (ES-T)
- Principled signature (ES-EPES)
- Signature with references (ES-C)
- Signature with protected references (ES-X)
- Long-term signature (ES-XL)
- Archive signature (ES-A)
Crypto Hardware Support
- Working with PKCS11 compatible smart cards and sticks
- Working with hardware security modules (HSM)
Crypto Features
- Working with X.509 v3 certificates prepared with RSA and elliptic curve algorithms
- SHA-2 family of message digest algorithms
Offered Advantages
- E-signature standards: Full compliance with international and national e-signature standards, laws, regulations and regulations
- Full compliance with PKI standards, effortless access to certificate and key services
- High-tech: Use of smart cards/sticks and HSM for high-level security
- National software compatible with international security standards
- Mobile technology: Interoperability on Android devices, use of Türk Telekom/Turkcell mobile signature
- Smart card support: Ability to transact with smart cards of different brands. Faster transaction on AKIS smart cards with APDU
- Ease of use and Turkish support
Timestamp Support
- Ability to check the correctness of the timestamp signature
- Access to all relevant information of a timestamped document
Other Public Key Infrastructure Services
- X.509 certificate validation
- X.509 certificate-based encryption
- Mobile signature


ESYA ZD SERVER / ESYA Timestamp Server
- Product information
- Features
- Technicial Features
- Answers
Time Stamp is a security data defined by an international standard and legally valid in order to prove the existence of electronic data on a specified date. The Timestamp Server generates timestamps in accordance with these standards for electronic data sent to it. The need to prove the date and time where a contract is signed, money is transferred, an application is made, etc. is vital for today's e-commerce and e-government applications.
In addition, a time stamp is required for all kinds of electronic data, such as a new drawing, design, photograph, idea, research, formula, algorithm, book, for which intellectual and proprietary usage rights are to be obtained. According to Electronic Signature Law No. 5070, Time Stamp refers to “the record verified by electronic signature by the electronic certificate service provider in order to determine the time when an electronic data was produced, changed, sent, received and/or recorded”.
ESYA Timestamp Server provides the following services:
- Timestamp conforming to the RFC 3161 standard
- Network Time Protocol (NTP) support
- Ability to work at high performance with the use of HSM and parallel processing of simultaneous requests
OS
- Windows 2008+
- Linux
Hardware and Software Requirements
- Intel/AMD Processor
- At least 8GB of RAM
- Oracle 11g or PostgreSQL 9.4 and higher database server
- Java 1.8+
Supported Standards
- RFC 3161 (Internet X.509 PKI Timestamp Protocol)
- ETSI TS 102 023 Timestamp Authority Policy Requirements
- X.509 v3 Certificates
Basic Security Services
- Timestamp signing process using X.509 Certificates and public key algorithms
- Authenticate client using PKCS 5
- Archiving the timestamp
Certificate and Crypto Features
- RSA and ECDSA algorithms support for timestamp signature
- Use of AES encryption algorithm
- Use of the SHA-1 and SHA-2 family of hash algorithms
Crypto Hardware Support
- The timestamp server does the signing in the hardware security module (HSM)
Standards Compliance
Timestamp Server PKIX RFC 3161 (Internet X.509 PKI Time Stamp Protocol) security standards compliant with the Electronic Signature Law No. 5070 generates a valid Timestamp.
Advanced Customer Management
With its advanced customer management interface, the Timestamp server can receive customer applications, add credit to defined customers, and respond to timestamp requests according to defined customer information.
Archiving Timestamp Files
The Timestamp Server can archive the timestamps it generates for later verification.
Advanced Cryptographic Algorithm Support
Timestamp Server supports advanced signing algorithms such as RSA and ECDSA, and the SHA-2 family of hash algorithms.
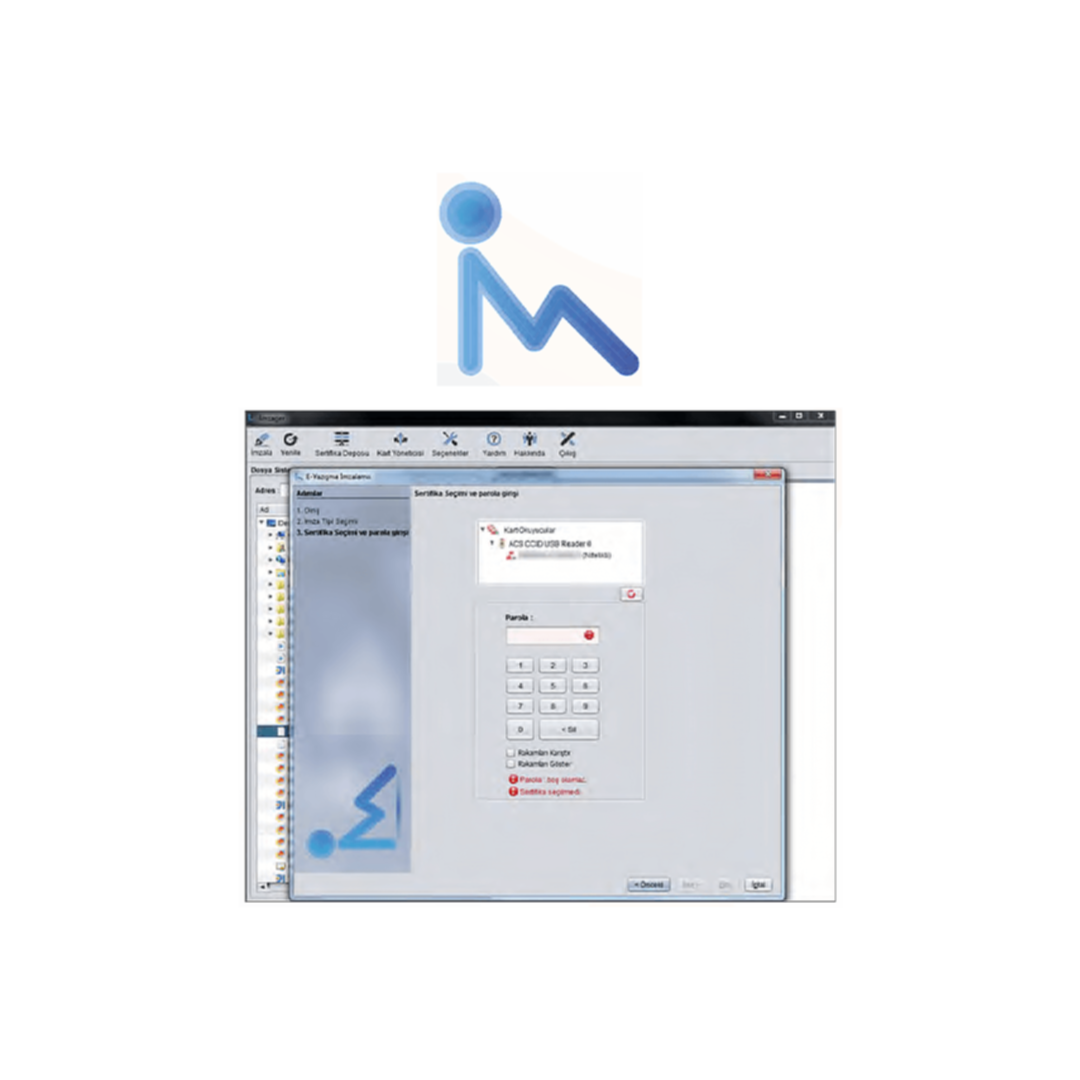
İMZAGER - Desktop Signing Application
- Product information
- Technicial Features
İMZAGER application is a helpful application that enables creating electronic signatures, viewing signatures in existing electronically signed documents, adding signatures and managing signatures. İMZAGER has been developed for software developers who develop electronic signature applications rather than corporate use.
Supported Standards
- ETSI TS 101 733 CAdES e-signature format
- ETSI TS 101 903 XAdES e-signature format
- ETSI TS 102 778 PADES e-signature format
- E-Correspondence Version 1.0 Support
- X.509 v3 certificates
- X.509 v2 certificate revocation lists (CRL/CRL)
- RFC 5280 certificate validation
- RFC 2560 online certificate status protocol (CISDUP/OCSP)
- RFC 3161 timestamp
Crypto Features
- Working with X.509 v3 certificates prepared with RSA and Elliptic Curve Algorithms
- SHA-2 family of message digest algorithms
Crypto Hardware Support
- Working with PKCS11 compatible smart cards and sticks
- Working with hardware security modules (HSM)

Network HSM Network Hardware Security Module
- Product information
- General Features
- Technicial Features
- Contact address
BILGEM Network HSM is a device developed to perform cryptographic operations such as encryption, signing, signature verification and hashing over a network with high performance and security. The communication between the device and the client is carried out over secure channels established by mutual authentication. High security is provided for these sensitive assets as the keys used in the transactions are stored within the cryptographic boundary with physical attack protection. Critical security operations such as initialization, backup, software update, user authentication are performed after authorization and authentication based on the national Smart Card Operating System AKİS. The device also offers a national solution to key generation with its national random number generator.
Management
- Remote device management
- GUI and command line administration program for remote administration
- 4.3 inch touchscreen for on-device management
- M-of-N admin verification on critical transactions
- Keeping transaction records
- Up to 256 PKCS#11 slots
- Up to 32 client connections
- Backup and restore
Performance
- RSA 2048-bit signing 520 ops/second
- RSA 4096-bit signing 110 ops/second
- ECDSA 256-bit prime signing 1600 ops/second
Physical Interface
- Gigabit Ethernet
Supported Operating Systems
- Linux, Windows
Our Projects through the Eyes of Management
- Remote device management
- GUI and command line administration program for remote administration
- 4.3 inch touchscreen for on-device management
- M-of-N admin verification on critical transactions
- Keeping transaction records
- Up to 256 PKCS#11 slots
- Up to 32 client connections
- Backup and restore
PERFORMANCE
- RSA 2048-bit signing 520 ops/second
- RSA 4096-bit signing 110 ops/second
- ECDSA 256-bit prime signing 1600 ops/second
PHYSICAL INTERFACE
- Gigabit Ethernet
SUPPORTED OPERATING SYSTEMS
- Linux, Windows
Communication and Customer Support
hsmdestek@tubitak.gov.tr













