BİLGEM
Cryptology
SIR-II / Encrypted USB Memory Device
- Product information
- Features
- Technicial Features
SIR-II is an encrypted USB memory device serving a single user, which securely stores all the data uploaded to it by encrypting it with its hardware structure. The device, which has 64 GB memory data carrying capacities, has a read-write speed of 10 MB / s.
The device ensures the security of the data loaded into the flash memory. Ensuring the security of the data during reading or writing from the computer to which the device is connected is out of the scope of protection.
Encrypted USB Memory Device serves a single user. Another user cannot access the encrypted data in the device by using their own card. It has many security measures such as emergency delete and tamper switch. Device login, user login, user card active and USB connection status can be observed with the audible warning and the light indicators on it.
With the write-protect switch on the device, it can be prevented from writing data to the device when requested. The device obtains its power via the USB connection interface and does not need any other power connection. There is a battery so that the cryptographic keys can be stored in memory even when there is no power. This battery is charged via the USB connection interface when the device is connected to the computer, and with a fully charged battery, the device can store the data in it for at least 6 months. The device is designed considering the architecture based on red-black separation for COMSEC, EMC, EMI and TEMPEST safety. The case is impact resistant.
- 12-keypad, 4 lamps each with dual color
- 1 buzzer, 1 emergency clear key, 1 write protect key
- 1 user smart card reader interface
- Platform independent - Windows (2000+), Linux (Kernel 2.4 and above) platforms
- Total 64GB data storage capacity
- Plug-and-play
- Dimensions: 51 x 91 x 14 mm
- Weight : 90 g
EKADAS-II Crypto Key Management Infrastructure
- Product information
- Features-1
- Features-2
EKADAS-II (Electronic Crypto Key Distribution System) Crypto Key Management Infrastructure enables the centralized or distributed generation of all kinds of sensitive crypto material and its fast, reliable and scalable distribution to the planned usage locations.
It has been designed keeping in mind the criteria of flexibility, modularity, speed, security and scalability. Thanks to the Updatable Security Module, it can easily adapt to different security protocol and algorithm needs. In addition to the traditional Electronic Key Management System capabilities, it offers integrated key management with other management systems and combines crypto key management systems under a single roof.
- HVTC, which is the key carrying and loading device used at the endpoints of the system, provides all the features of the new generation key loading devices and includes additional capabilities for national use.
- The system, which can operate with full redundancy, allows portable end switch loading devices to remotely receive sensitive crypto materials by using PSTN, H/F, Satellite and Ethernet connection alternatives.
- Secure distribution of all kinds of sensitive information (crypto key -symmetric/asymmetric-, certificate, software, code, password, configuration/administration information, file, message, etc.)
- High quality key generation (with a combination of quantum and traditional RSU techniques)
- Transition from Electronic Key Management System concept to Key Management Infrastructure concept that can be integrated with all other management systems
- Supporting complex key management of next generation crypto devices
- Distribution and accounting of crypto materials by inventory of crypto devices
- Integration with other systems using the Common Key Management Framework (OAYÇ)
- Reducing the diversity of key management systems/components and bringing them together under the umbrella of EKADAS-II
- Ability to generate keys for over a hundred crypto device types
- Support for operators to design and manage their own key formats
- Advanced smart key accounting
- Ability to define cryptographic and managerial relationships between sensitive materials
- Ability to meet complex key management needs
- Software update of crypto devices securely remotely
- Centralized management of crypto devices key upload profiles
- Platforms
- Crypto devices,
- Key types,
- Key slots,
- Installation interfaces and parameters, installation packages, etc.
- Fast response time with online and star connected topology
- Interoperability with NATO IEKMS
- Supporting Platform Key Management Systems included with A400M and JSF aircraft
- Reliable architecture centered on redundant management
- Built-in secure messaging support
It is subject to the sales license to be given by the Ministry of National Defense.


KAYC-S - Crypto Key Loading Device
- Product information
- Features
- Technicial Features
NATIONAL KEY LOADING SOLUTIONS
KAYC-S is a cryptographic device that has the features of storing, transporting and transferring data in encrypted form with cryptographic keys received with standard interfaces and protocols (DS-101, DS-102, MILAY) and key uploading/end crypto devices.
KAYC-S device, which is activated by being defined in the EKADAS-II (Electronic Crypto Key Distribution) System, can receive keys from EKADAS-II or other systems. The device has the ability to receive cryptographic data and key from HVTCs (Sensitive Data Transport Device), which are EKADAS-II terminal devices, or other supported data transport devices [AN/CYZ-10 (DTD), DTD2000 (SDS), Simple Key Loader (SKL)] and key loading devices (KYK-13, KAYC-10, KAYC-32, KAOC-8, KOI-18, MILAY EAYC) with standard interfaces via the upload interface. It processes the cryptographic data and keys it receives with security-enhancing measures such as integrity control and encryption, securely stores it and uploads it to various key loading/transport and end crypto devices. It has the ability to securely record the accounting information of the keys and transfer them to the EKADAS-II System.
Data security in the device is ensured by the system architecture based on red/black separation, filtering, tamper protection and emergency deletion mechanism. KAYC-S is a tactical device and complies with COMSEC, EMI/EMC, TEMPEST requirements.
INTERFACES
- Via 6 pin connector
- DS-102 (EKMS-308F)
- DS-101/RS-485 (EKMS-308F)
- DS-101/RS-232-D (EKMS-308F)
- MILAY
- Usage for “NATIONAL CONFIDENTIAL” and lower data privacy levels
- National format key storage and loading
- User-friendly graphical interface
- Electrically and mechanically red/black insulation
- 320 x 240 TFT liquid crystal display and 7-entry keypad
- External keyboard interface (PS/2)
- Light and audible warnings
- Ability to create and initialize users from the EKADAS-II system
- Receiving cryptographic data from EKADAS-II system
- Ability to create, store and transfer accounting and transaction records to EKADAS-II system
- Ability to update software via EKADAS-II
- TAF approved crypto algorithms
- System-independent initialization capability (Free Mode)
- User access control with smart card and password
- Emergency erasable nonvolatile memory for preservation of cryptographic data and keys
- Emergency wiping when the device is in use or off
KAYC-S/N - Crypto Key Loader/NATO
- Product information
- Features
- Technicial Features
SOLUTIONS TO INSTALL NATO KEYS
KAYC-S/N is a cryptographic device that has the features of storing, transporting and transferring cryptographic keys encrypted with the interfaces and protocols defined by the EKMS-308F standard, and transferring them to various key loading/end crypto devices in NATO inventory.
KAYC-S/N has SECAN security approval at all NATO secrecy levels and has been approved by the “Military Comitee” and has been awarded the title of NATO device.
The device stores the red or black key and cryptographic data it receives from local government devices (LMD/KP, DMD), data transport devices [(AN/CYZ-10 (DTD), DTD2000 (SDS), Simple Key Loader (SKL), EKATAC/EKAYUC)] and key loading devices (KYK-13, KAYC-10, KAYC-32, KAOC-8, KOI-18) securely with integrity control and encryption. It transfers the keys to the data transfer devices in red or black, uploads them to the end devices and upload devices.
It has the ability to save the accounting information of the keys securely and transfer them to local management devices such as LMD/KP, DMD. The device supports CT3 (Common Tier3) application software infrastructure.
Data security in the device is ensured by the system architecture based on red/black separation, filtering, tamper protection and emergency deletion mechanism. KAYC-S/N is a tactical device and complies with COMSEC, EMI/EMC, TEMPEST requirements.
- Usage for “NATO TOP SECRET” and lower data privacy levels
- NATO approved crypto algorithm
- Storing, decrypting and loading NATO-formatted (encrypted/non-encrypted) keys
- User access control with smart card and password
- User-friendly graphical interface
- Electrically and mechanically red/black insulation
- 320 x 240 TFT liquid crystal display and 7-entry keypad
- External keyboard interface (PS/2)
- Light and audible warnings
- Ability to create, store and transfer accounting and transaction records
- Emergency erasable nonvolatile memory for preservation of cryptographic data and keys
- Emergency wiping when the device is in use or off
INTERFACES
Via 6 pin connector
- DS-102 (EKMS-308F)
- DS-101/RS-485 (EKMS-308F) - end-to-end or bus structure
- DS-101/RS-232-D (EKMS-308F)


HVTC - Sensitive Data Transport Device
- HVTC
- Product information
- Features-1
- Features-2
It is a new generation upload device that combines crypto key processing (strategic) and transport device (tactical) capabilities in a single device. Thanks to its updateable security module component, it can adapt to scenarios that require other protocols and algorithms. It is designed for tough tactical field conditions. It allows to perform complex key management functions with its user-friendly GUI and touch screen capabilities.
- Secure electronic crypto key and data transfer from EKADAS-II (Electronic Crypto Key Distribution System) system via WAN interface
- Uploading/receiving crypto keys and data in NATO and national formats to NATO and national key transport devices and crypto devices
- Legacy and modern crypto key support
- Crypto key accounting and detailed transaction/event records
- Profile database of remotely managed Tier3 devices
- Platforms
- Crypto devices
- Key types, key loading slots, key segment assignments
- Download interfaces and parameters
- Key relationships
- Secure communication interfaces (between Tier2 and Tier3 layers)
- PSTN, HF/UHF, SATCOM, Ethernet
- Key loading interfaces
- DS101,
- DS102,
- MILAY,
- RS232,
- TapePuncher
- USB 2.0 (Smart card, USB memory, CD/DWDRW, Printer)
- Ethernet (Integration with other systems using special protocol)
- High storage capacity (~32GB)
- Rule and role-based access control
- Two-factor authentication (PIN and smart card)
- User-friendly, icon-based interface (Multi-language support)
- Shockproof PCAP+ touchscreen (16:9, 7 inch color TFT WSVGA)
- High screen resolution (1024×600)
- Touch patterns with special meaning
- Readable in sunlight
- Can be used with gloves
- Built-in crypto processor (able to host and run 1000+ crypto algorithms)
- Agile crypto support (updatable crypto algorithms)
- Remote/close secure software/firmware update
- Tamper proof
- EMI/EMC Compliant (MIL-STD 461E)
- TEMPEST Compatible ( SDIP-27/1 Level A)
- Waterproof and dustproof (IP67)
- Operating temperature: Lowest -20 °C, Maximum +60 °C
- Storage temperature: Lowest -30 °C, Maximum +70 °C
- Physical dimensions: 23.2 cm x 15.8 cm, 4.9 cm, ~2 kg
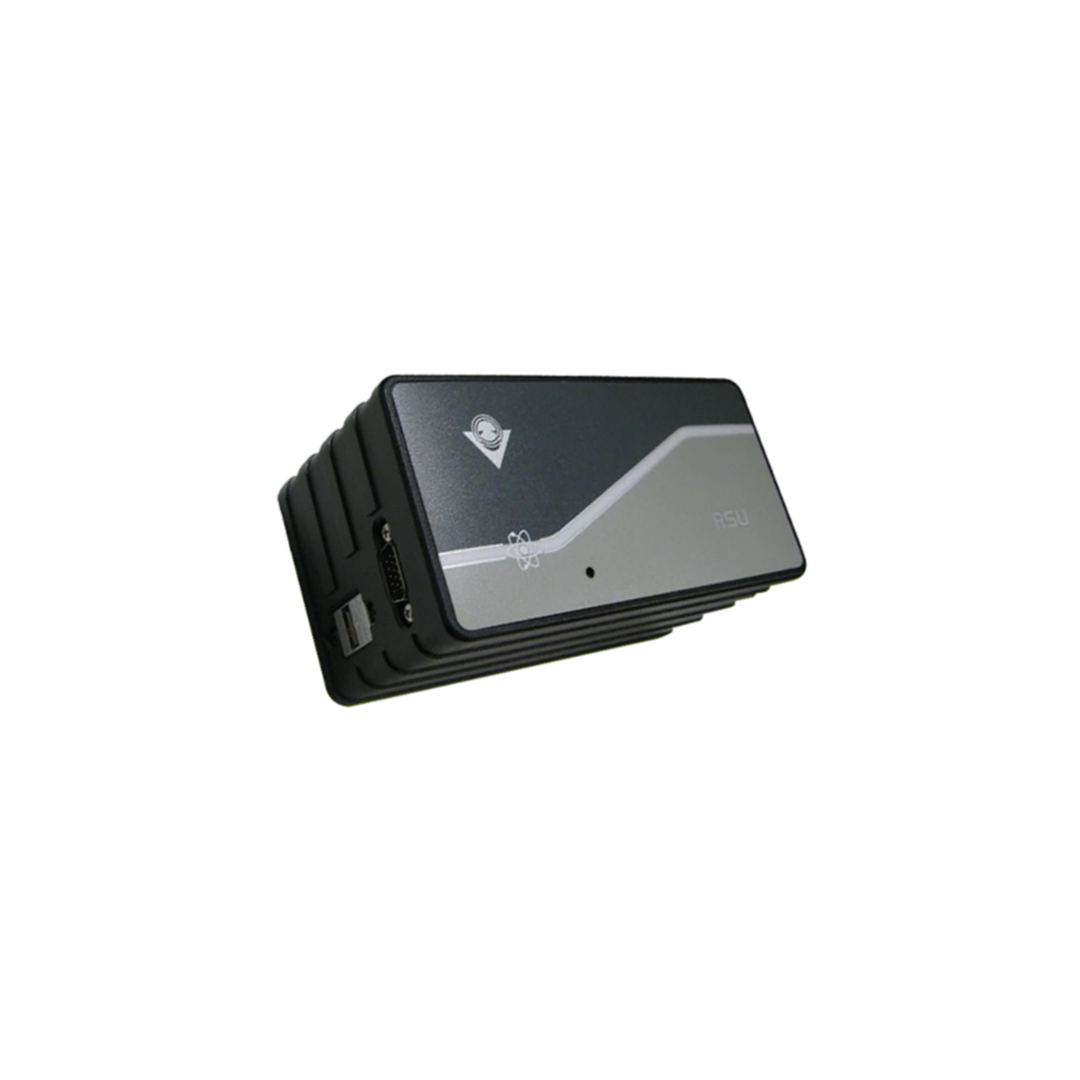
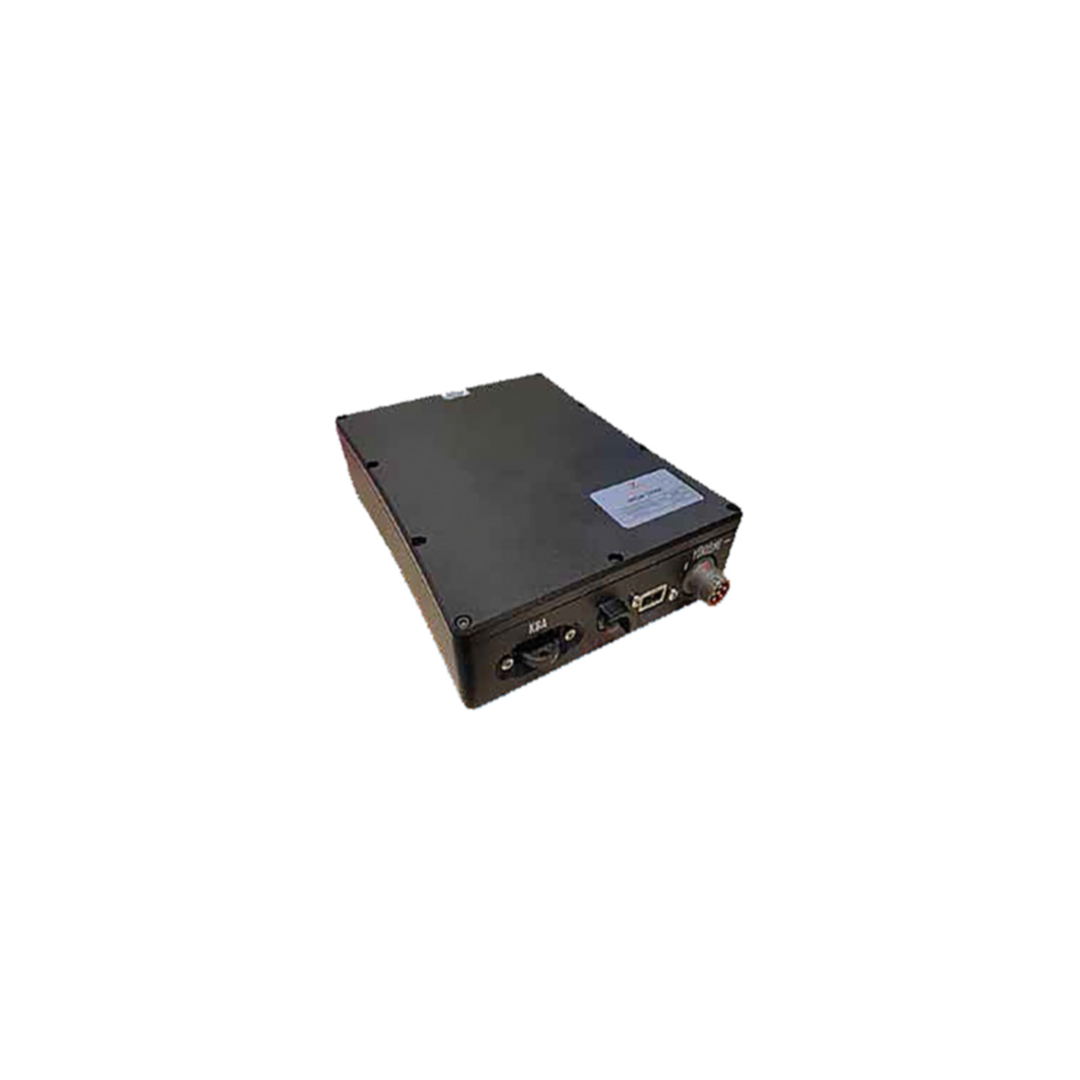
QUANTUM RSU - Quantum Based Random Number Generator
- Product information
- Technicial Features
The Quantum Random Number Generator device makes the random data obtained from the quantum source contained in it more reliable by passing it through various mathematical tests and mixer functions and gives it via the USB 2.0 interface.
The fact that quantum mechanical systems are random in nature is the biggest advantage of quantum random number generators. Especially in cryptographic systems where security is very important, using QUANTUM RSU gives better results than other random generators in terms of security of the whole system.
- Input voltage: 12V
- Typical power consumption: 4 W
- Interface: USB 2.0
- Max data rate (Tested throughput rate): 12 Mbit/s
- Typical data rate (Tested throughput rate): 4 Mbit/s
- Physical size: 80mm x 80mm x 150mm
- Weight: 500 grams
- Operating temperature: 0- 35 °C
- TEMPEST feature: Yes
- COMSEC feature: Yes
- Outer case: Aluminum
GM - Security Module
- Product information
- Features-1
- Features-2
GM (Security Module) is a general purpose hardware security module that offers cryptographic data generation/processing and secure data storage capabilities. It is designed as a portable device with the aim of military and commercial use. The device complies with COMSEC, EMI/EMC, TEMPEST standards. Since security mechanisms are predominantly modular and software-based, they can be easily updated and integrated into security products without requiring hardware changes. With its USB interface, it can be easily integrated into any platform as a component that completes security. It can exchange data securely both with the platform it is installed on and with external transport devices and data transport environments. Data exchange is supported with GM upload interfaces, smart card, USB memory, crypto and military key carrying devices with supported interfaces.
- High quality key generation
- Ability to add/update new crypto algorithms
- Crypto Device private key encryption/decryption/signing capability
- Receiving and uploading electronic key or confidential data to initialize itself and system devices via key upload interfaces
- Key format support compatible with national key formats
- Legacy and modern crypto key support
- Crypto key accounting and detailed transaction/event records
- Communication with Key Generation and Distribution Servers (USB 2.0)
- Key loading interfaces
- DS101 (RS485/RS232)
- DS102
- MİLAY
- USB 2.0 (Smart card, USB memory)
- Built-in hardware-based TRSU (True Random Number Generator)
- Support for working with external RSU
- High storage capacity (~32GB)
- Ability to host and run multiple crypto algorithms
- Updatable crypto algorithms support
- Software update
- Authentication with Crypto Initialization Key
- Tamper resistance
- Attachable and detachable
- Crypto Permission Key
- EMI/EMC compliant (MIL-STD-461E)
- TEMPEST compliant (SDIP-27/1 Level A)
- COMSEC compliant
- Operating temperature: -20 °C to +60 °C
- Storage temperature: -30 °C to +70 °C
- Physical Dimensions (Excluding Connector): 209 mm x 153 mm x 46 mm (±10%) ~1.4 kg
KMA - Cryptographic Architecture and Algorithm Design
- Product information
- Activities
Cryptography is the science of providing information security with mathematical methods. Cryptography provides solutions to security needs, such as data privacy, data integrity, non-repudiation, authentication, access control. These solutions are implemented in all places where information security and privacy are required, from smart cards to satellites, from network security devices to sensors. Cryptographic structures (algorithms, protocols and architectures) form the basis of these services.
Experienced and qualified researchers specialized in fields such as mathematics, statistics and electronics are required to develop unique cryptographic structures. TÜBİTAK BİLGEM UEKAE has been operating in this field since the 1980s and meets the needs of our country.
- Cryptographic algorithm (encryption, digest, key wrapping, text authenticating codes, etc.) design
- Cryptographic protocol (authentication, key agreement, etc.) design
- Cryptographic architecture (device and/or all cryptographic structures in the system) design
- Noise processing function design (used in random number generators)
- Training and consultancy on cryptography
It is subject to the sales license to be given by the Ministry of National Defense.














